2025 Cross-Chain Security Audit Guide
2025 Cross-Chain Security Audit Guide
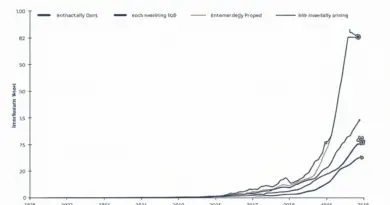
According to Chainalysis, a staggering 73% of global cross-chain bridges contain vulnerabilities. In this rapidly evolving crypto landscape, joining the HIBT Bitcoin Discord community can provide you with real-time insights into these emerging threats and how to navigate them safely.
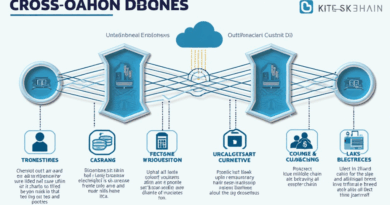
What are Cross-Chain Bridges?
Imagine you are at a currency exchange booth while traveling abroad. Just like exchanging your cash for local currency, cross-chain bridges allow users to transfer tokens between different blockchain networks. However, just like currency booths can run out of certain currencies or be less trustworthy, cross-chain bridges can have their vulnerabilities.
Understanding the Risks
Every time you use a cross-chain bridge, think of it as walking through a crowded marketplace. You might run into pickpockets if you’re not careful! The risks mainly include smart contract flaws and security loopholes that can lead to losing your assets. The key is to stay alert; following discussions in the HIBT Bitcoin Discord community can help you identify the safest options.

Best Practices for Users
To keep your assets safe while using these bridges, employ practices like multi-signature wallets and regular audits, much like checking your bags regularly while shopping. Joining communities like HIBT Bitcoin Discord can also connect you with experienced traders who can share valuable advice.
Future Trends in Cross-Chain Security
Looking towards 2025, we predict a shift towards enhanced security protocols, similar to how banks adopt more advanced technologies for protecting your funds. Innovations such as zero-knowledge proofs could revolutionize transaction privacy in cross-chain trading. Dive into discussions about these upcoming technologies with fellow members in the HIBT Bitcoin Discord community.
In conclusion, as the blockchain world evolves, staying informed and connected through resources like the HIBT Bitcoin Discord community is essential. For a deeper understanding, download our comprehensive security toolkit, which includes everything from risk assessments to best practices!