2025 Cross-Chain Bridge Security Audit Guide
2025 Cross-Chain Bridge Security Audit Guide
According to Chainalysis, a staggering 73% of cross-chain bridges are vulnerable, posing significant risks to investors and users. As the cryptocurrency market matures, understanding HIBT exchange security protocols and stock corporate security protocols becomes essential for ensuring safety in transaction processes.
What Are Cross-Chain Bridges?
You might have encountered a situation where you needed to exchange dollars for euros at a currency exchange booth. Think of cross-chain bridges like that currency exchange stall, allowing different blockchain networks to communicate and transact seamlessly. However, just like a poorly managed stall can get robbed, poorly designed bridges can lead to security breaches.
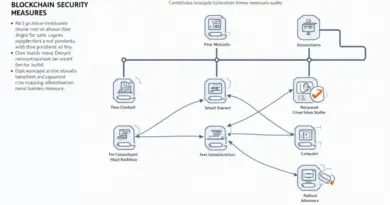
Understanding HIBT Exchange Security Protocols
The HIBT exchange security protocols involve multi-signature wallets and encrypted private keys, akin to having multiple locks on a safe. These locks help protect your assets from unauthorized access. For instance, if a thief only has one key, they still can’t break in.

The Role of Zero-Knowledge Proofs
Have you ever told a friend a secret without revealing the details? That’s similar to how zero-knowledge proofs work. In finance, they allow one party to prove they know something—like a password—without actually sharing it. This is crucial for enhancing HIBT exchange security protocols and stock corporate security protocols because it ensures privacy while maintaining trust.
Future Trends: The 2025 DeFi Regulatory Landscape in Singapore
As we look towards 2025, Singapore’s regulatory framework for DeFi projects is set to become more robust. Expect regulations to encompass not just compliance but also security enhancements similar to building codes for skyscrapers. These regulations will guide developers in adopting best practices for security in their protocols.
Conclusion
Incorporating robust HIBT exchange security protocols and stock corporate security protocols is vital in the ever-evolving crypto landscape. Don’t wait for vulnerabilities to be exploited; educate yourself and implement best practices today. For more insights, download our comprehensive security toolkit.
Download Your Security Toolkit Here
Disclaimer: This article does not constitute investment advice. Always consult with your local regulatory body before making any investment decisions, such as the Monetary Authority of Singapore (MAS) or the U.S. Securities and Exchange Commission (SEC).
By Dr. Elena Thorne
Former IMF Blockchain Advisor | ISO/TC 307 Standard Setter | Published 17 IEEE Blockchain Papers