2025 Cross-Chain Security Audit Guidelines
2025 Cross-Chain Security Audit Guidelines
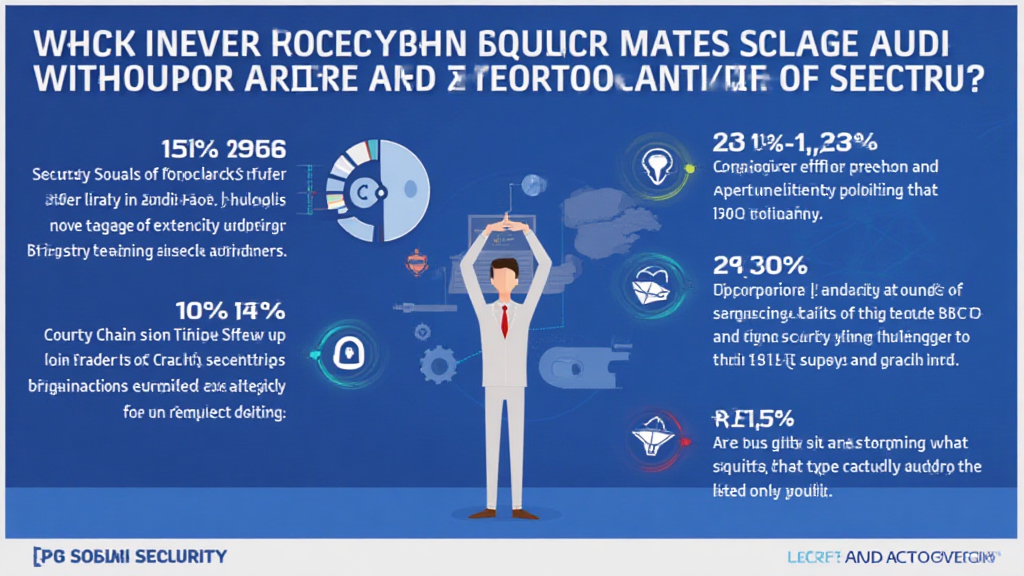
According to Chainalysis data, around 73% of cross-chain bridges worldwide have vulnerabilities. As the cryptocurrency landscape evolves, understanding the intricacies of cross-chain operations becomes vital, especially if you’re looking into trading stocks via platforms like HIBT. Let’s dive into what this means for you.
1. What is a Cross-Chain Bridge?
Think of a cross-chain bridge like a currency exchange booth at an airport. Just as you would swap pounds for euros before a holiday, cross-chain bridges allow different blockchains to communicate and exchange assets. This is essential in our global digital economy, especially when exploring stocks on the HIBT trading platform.
2. Understanding Vulnerabilities
If 73% of these bridges have a flaw, what does that mean for your assets? Vulnerabilities could be potential loopholes that hackers exploit. It’s like a broken lock on a front door; you wouldn’t leave your house unsecured, right? Always ensure the bridges you use are secure, especially when trading on platforms like HIBT.
3. Key Security Measures
To avoid risks, platforms like HIBT should implement multi-signature wallets and frequent audits. Just like how car owners check their vehicles before a long drive, traders should verify the security measures of their trading platforms. This extra step can save you headaches in the long run.
4. Future Trends in Cross-Chain Security
Looking towards 2025, regulatory trends will likely tighten around cross-chain operations. Countries like Singapore are already positioning themselves to enhance DeFi regulations. It’s essential for traders to stay informed about these developments to safeguard their investments effectively.
In conclusion, navigating the world of cryptocurrency trading requires diligence, especially with vulnerabilities in cross-chain bridges. By staying informed and cautious, traders can ensure their assets are protected. For more insights, don’t forget to download our comprehensive toolkit for cross-chain security.